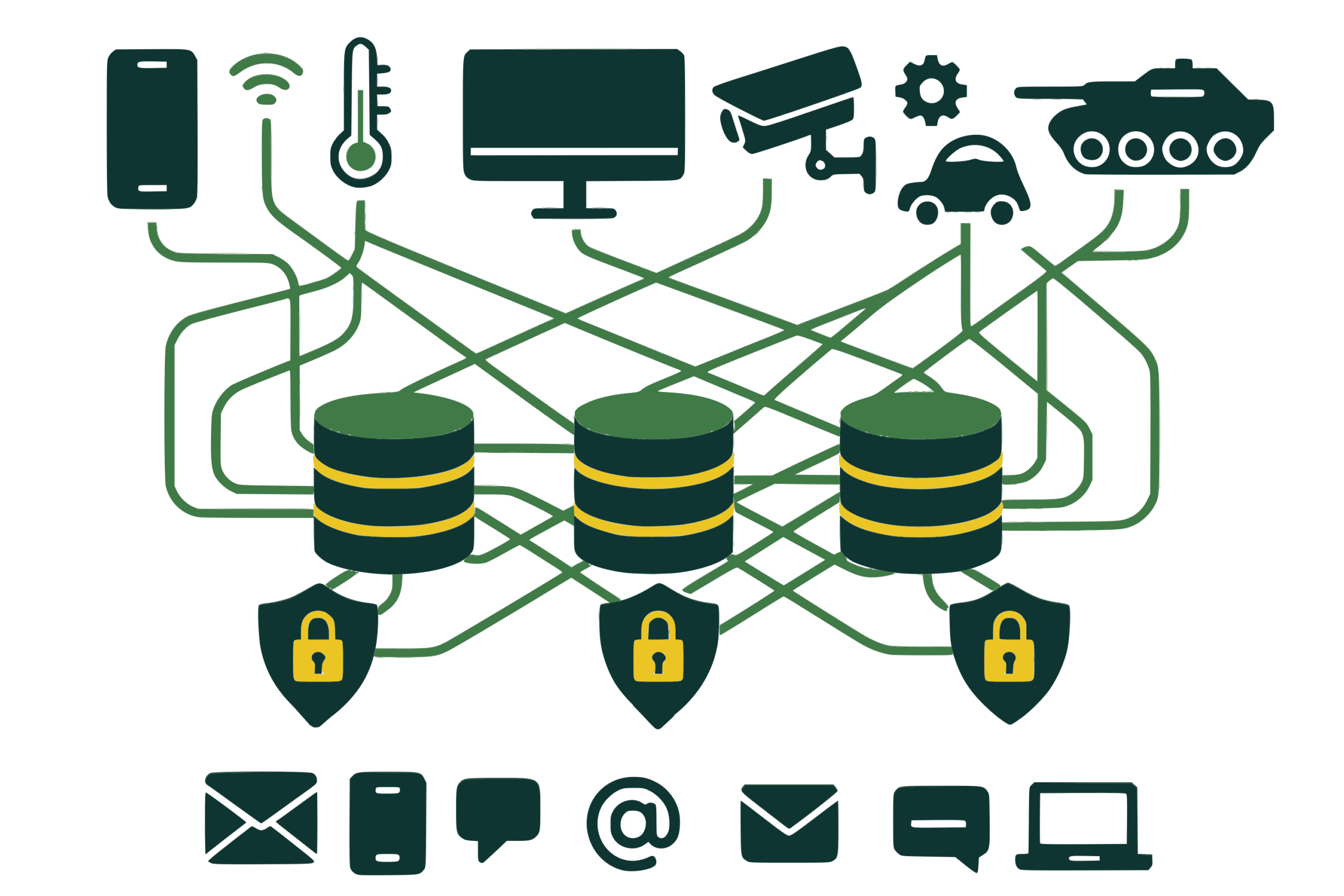
Zero Trust
Quantum Resistance
Mission Ready
The best thing about GABRL is
being able to disappear completely
Nation-state adversaries are stockpiling your encrypted traffic today, waiting for the quantum computers of tomorrow. When they arrive, decades of sensitive government data will be exposed overnight.
GABRL stops the threats of tomorrow, today.
NIST SP 800-207
Policy Engine + PEPs
continuous assessment
NSM-10
No long-lived keys
quantum-robust AES
FIPS 140-2/3
All cryptographic modules validated
RMF / NIST 800-53
Aligns with AC, IA, SC families
ATO ready
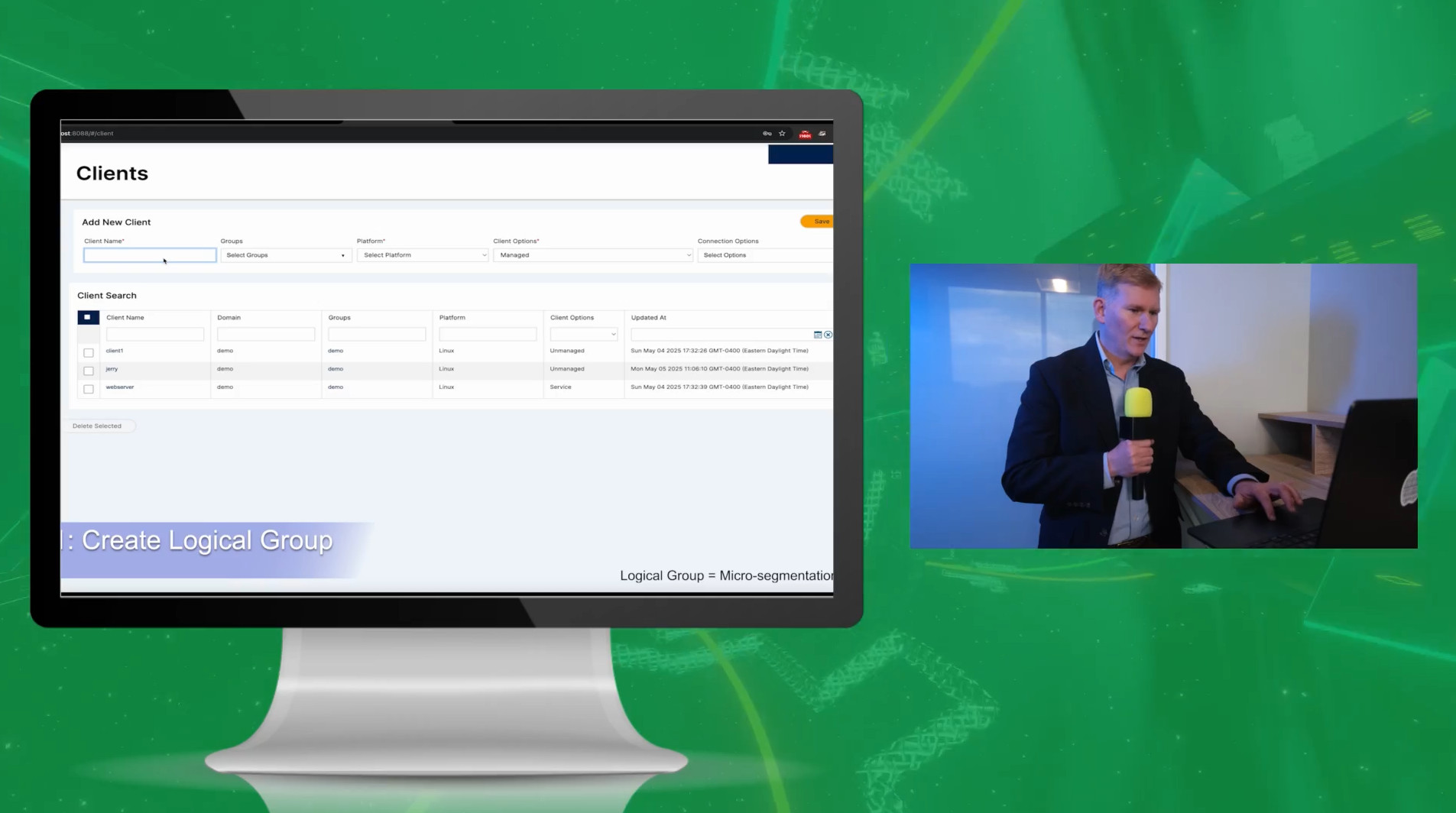
Zero-Trust Architecture
L3 micro-seg
Per-session validation
Architectural PKI
Zero session overlap
Constant key rotation